The main MD5 algorithm operates on a 128-bit state, divided into four 32-bit words, denoted A, B, C and D. These are initialized to certain fixed constants. The main algorithm then operates on each 512-bit message block in turn, each block modifying the state. The processing of a message block consists of four similar stages, termed rounds; each round is composed of 16 similar operations based on a non-linear function F, modular addition, and left rotation. Figure 1 illustrates one operation within a round. There are four possible functions F; a different one is used in each round:
What is MD5?
MD5 is Message Diggest 5, a cryptographic methode with 128 bit hash value.
MD5 Checksum
What is MD5 checksum?
MD5 checksum is Sum of signature code that present in 32 hexadecimal, e.g software bit check (to ensure free from injection of malware).
How to check MD5 sum?
-Linux
e.g: here MD5 checksum info of Gparted iso image from Gparted site,
MD5SUMS
9c2c06513b609bad55d18513704a8c4b gparted-live-0.4.6-1.iso
Open Terminal,
$mdsum gparted-live-0.4.6-1.iso
9c2c06513b609bad55d18513704a8c4b gparted-live-0.4.6-1.iso
-Windows Xp
e.g: check md5 for dune2000.exe (games)
Use Tools md5summer, choose create md5
MD5 Algorithm
MD5 processes a variable-length message into a fixed-length output of 128 bits. The input message is broken up into chunks of 512-bit blocks (sixteen 32-bit little endian integers); the message is padded so that its length is divisible by 512. The padding works as follows: first a single bit, 1, is appended to the end of the message. This is followed by as many zeros as are required to bring the length of the message up to 64 bits fewer than a multiple of 512. The remaining bits are filled up with a 64-bit integer representing the length of the original message, in bits. 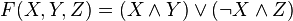



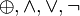 denote the XOR, AND, OR and NOT operations respectively.
denote the XOR, AND, OR and NOT operations respectively.
MD5 Pseucode
Pseudocode is a compact and informal high-level description of a computer programming algorithm (MD5 algorithm) that uses the structural conventions of a programming language, but is intended for human reading rather than machine reading.
e.g:
*************************************************************************************
//Note: All variables are unsigned 32 bits and wrap modulo 2^32 when calculating
var int[64] r, k
//r specifies the per-round shift amounts
r[ 0..15] := {7, 12, 17, 22, 7, 12, 17, 22, 7, 12, 17, 22, 7, 12, 17, 22}
r[16..31] := {5, 9, 14, 20, 5, 9, 14, 20, 5, 9, 14, 20, 5, 9, 14, 20}
r[32..47] := {4, 11, 16, 23, 4, 11, 16, 23, 4, 11, 16, 23, 4, 11, 16, 23}
r[48..63] := {6, 10, 15, 21, 6, 10, 15, 21, 6, 10, 15, 21, 6, 10, 15, 21}
//Use binary integer part of the sines of integers (Radians) as constants:
for i from 0 to 63
k[i] := floor(abs(sin(i + 1)) × (2 pow 32))
//Initialize variables:
var int h0 := 0x67452301
var int h1 := 0xEFCDAB89
var int h2 := 0x98BADCFE
var int h3 := 0x10325476
//Pre-processing:
append "1" bit to message
append "0" bits until message length in bits ≡ 448 (mod 512)
append bit /* bit, not byte */ length of unpadded message as 64-bit little-endian integer to message
//Process the message in successive 512-bit chunks:
for each 512-bit chunk of message
break chunk into sixteen 32-bit little-endian words w[i], 0 ≤ i ≤ 15
//Initialize hash value for this chunk:
var int a := h0
var int b := h1
var int c := h2
var int d := h3
//Main loop:
for i from 0 to 63
if 0 ≤ i ≤ 15 then
f := (b and c) or ((not b) and d)
g := i
else if 16 ≤ i ≤ 31
f := (d and b) or ((not d) and c)
g := (5×i + 1) mod 16
else if 32 ≤ i ≤ 47
f := b xor c xor d
g := (3×i + 5) mod 16
else if 48 ≤ i ≤ 63
f := c xor (b or (not d))
g := (7×i) mod 16
temp := d
d := c
c := b
b := b + leftrotate((a + f + k[i] + w[g]) , r[i])
a := temp
//Add this chunk's hash to result so far:
h0 := h0 + a
h1 := h1 + b
h2 := h2 + c
h3 := h3 + d
var int digest := h0 append h1 append h2 append h3 //(expressed as little-endian)
//leftrotate function definition
leftrotate (x, c)
return (x <<>> (32-c));
*************************************************************************************
MD5 authentication
MD5 is used too for ospf authentication that prevent stanger from receive routing updates.
e.g:
rachmat(config)#int f0/0
rachmat(config-if)#ip add 74.125.33.9 255.255.255.0
rachmat(config-if)#ip ospf authentication
rachmat(config-if)#ip ospf authentication-key rxnuxer
rachmat(config-if)#ip ospf message-digest-key 7 md5 rxnux3r
rachmat(config)#router ospf 1
rachmat(config-router)#router-id 10.10.10.1
rachmat(config-router)#netw 74.125.33.0 0.0.0.255 area 1
rachmat(config-router)#area 1 authentication message-digest
MD5 Decryptor
Web based tool for found the real text or source text from md5
e.g: md5 for rachmat is 2dbc7dd7e9524ddff1157d2e3df10aeb
where rachmat is the source text and 2dbc7dd7e9524ddff1157d2e3df10aeb is md5crypt.
Just decrypt md5crypt to get source text
source:
http://therachmat.blogspot.com
http://en.wikipedia.org/wiki/MD5
http://www.md5summer.org
http://www.md5decrypter.com
Subscribe to:
Post Comments (Atom)


8 comments:
ngantuk euy bikin artikel ini, semoga bermanfaat
wah, dikira MDG's. lucu juga referensinya blog ini juga
Manyab gan onfonya nich..semangat trus..
Salam Damai Indonesia
unndo15 with Acatrazz
P E A C E
kapan ya do follow
@Lesly, paan tuch MDG
@Peace, semangat juga buat Acatrazz
@Finance Blog, maksudna dofollow comment? blog ini udah ga dofollow comment lagi, coz kl do follow bnyk yg nyepam :D
salam sahabt
ehm..makasih atas kunjungannya ya..oh iya jadi tahu lebih banyak nich dapet segudang ilmu dari sini thnxs n good luck ya..
salam sahabt
ehm..makasih atas kunjungannya ya..oh iya jadi tahu lebih banyak nich dapet segudang ilmu dari sini thnxs n good luck ya..
Wah awam sekali nih sobat.. gak ngerti yg ginian hehee..
Post a Comment
leave comment here, thanks for visiting
[Friends Link] [Facebook] [Twitter]